February 15th, 2013
Make a script with this content:
Windows 2003:
DEL C:\”Documents and Settings\%username%\Local Settings\Temporary Internet Files”\*.* /Q /F /S
Windows 2008:
DEL C:\”Users\%username%\AppData\Local\Microsoft\Windows\Temporary Internet Files”\*.* /Q /F /S
Add is as an logoff script
Great on Terminal servers.
February 14th, 2013
Find this in regedit:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\AE1D439464EB1B8488741FFA028E291C\Patches\DAB7360D98CBBF4498895E7EF3AFC452′
The key “DisplayName” gives the version (SP and rollup)
Example: Update Rollup 6 for Exchange Server 2010 Service Pack 2 (KB2746164) 14.2.342.3
February 11th, 2013
All users desktop
C:\Users\Public\Desktop
(The Desktop folder is hidden)
All users start menu and programs:
C:\ProgramData\Microsoft\Windows\Start Menu
C:\Users\All Users
February 7th, 2013
The “list” zen.spamhaus.org combines all spamhaus.org’s filters including the PBL
PBL is a DNSBL database of end-user IP address ranges and this could give false positivs
Instead you could use: sbl-xbl.spamhaus.org
Rumors says, When Zen is used solely as the single test to block spam it could lead to false positives.
Configuration:
/etc/postfix/main.cf
Change:
smtpd_client_restrictions = permit_sasl_authenticated, reject_rbl_client zen.spamhaus.org
to:
smtpd_client_restrictions = permit_sasl_authenticated, reject_rbl_client sbl-xbl.spamhaus.org
Alternatives:
xbl.spamhaus.org
sbl-xbl.spamhaus.org
zen.spamhaus.org
bl.spamcop.net
/etc/Mailscanner/spam.lists.conf
Restart postfix and Mailscanner
February 7th, 2013
Download the ADMX/ADM files from here:
http://www.microsoft.com/en-us/download/details.aspx?id=18968
Extract the downloaded file.
Copy the content of the ADMX folder to this folder on the DC:
\\localhost\SYSVOL\domain.local\Policies\policydefinitions
Create the folder policydefinitions if it is missing.
The new policies are automatically replicated to all the DC’s.
And they are visible in GPMC
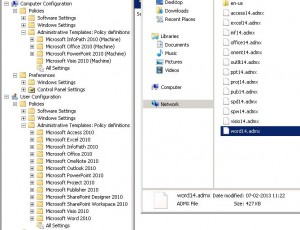
Remember this last step.
The old gpo’s is now missing. This is because the new “policydefinitions” folder is in control.
You need to copy the contents of: C:\Windows\PolicyDefinitions
from a DC to this folder – then the old polycy’s are back.
Remember, Widows update does not update this new store’s policy’s!
You need to do this by hand.
